Introduction
ISO 27001 is a key industrial standard in software development. It ensures that developers consider information security in all stages of the development process. Nowadays, information security is even more important because all solutions are moving to the Cloud platform. Overall, the information security management system of a business may be monitored, reviewed, maintained, and improved with the help of ISO 27001, and partner organizations and clients will surely feel more comfortable doing business with you. Some benefits of ISO 27001:
It shows third parties and stakeholders a demonstrated commitment to information security management.
It can offer a framework to guarantee the fulfillment of obligations under contracts, laws, and other legal obligations.
It gives the company a considerable competitive edge and may serve as a license to do business with specific firms in regulated industries.

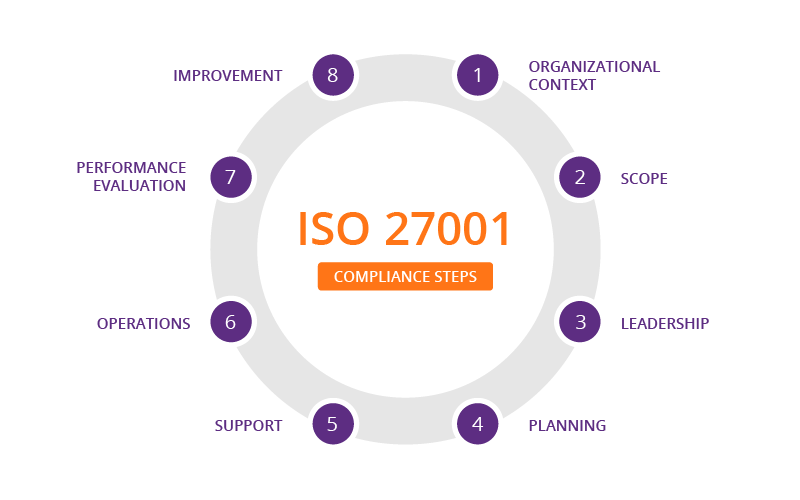
ISO27001
It specifies the requirements for establishing, implementing, maintaining, and continuously improving an information security management system (ISMS), with the goal of assisting organizations in making their information assets more secure. Following the successful completion of an audit, organizations that meet the standard's requirements can choose to be certified. The adoption of the recognized standards delivers a useful and significant message to consumers and business partners: this company does things the right way. The standards guarantee that a business's security risks are addressed cost-effectively.
According to the control of compliance (A. 18 Compliance) from ISO 27001, the process of Enterprise Application Management needs to comply with the legal and contractual requirements of the standard and it should be documented as per the “Statement of applicability”.
Data Protection
A legal framework known as the General Data Protection Regulation (GDPR) establishes rules for the gathering and handling of personal data from people who reside outside of the European Union (EU). The GDPR was approved in 2016 and fully implemented two years later. By holding businesses accountable for how they handle and treat this information, it aims to give consumers control over their own personal data. The rule is applicable regardless of where websites are located, so all websites that draw visitors from Europe must comply by it, even if they don't specifically target EU citizens when marketing products or services.
Last updated