Data Privacy & Security
Security Framework
"Security Framework" refers to frameworks that are designed to enable secure user identification which is needed if you want to include access control features, such as registration, login authentication, and authorization.
The ASP.NET Core Identity Framework builds upon the Entity Framework (described in the previous article) by providing classes, methods, etc. that enable secure user identification, so that you can use the access control features mentioned above in your .NET applications. There are two steps in the security framework process:
Verifying your identity: For every click to login in, the user sends request to the server. Then the application verifies the identity. After this, a token with serial number is created and saved as cookie in the web browser.
Encrypting the password: The second step of security framework is saving the user password in the database, but it is automatically encrypted into serial code.
Access control
Advantech implements physical and logical access controls across IT networks, IT Systems and services in order to provide authorized, granular, auditable and appropriate preservation of data confidentiality, integrity and availability in accordance with the IT Security Policy. Access controls systems are in place to protect the interests of all authorized users of Advantech IT systems, as well the ones provided by third parties, by creating a safe, secure and accessible environment in which to work.
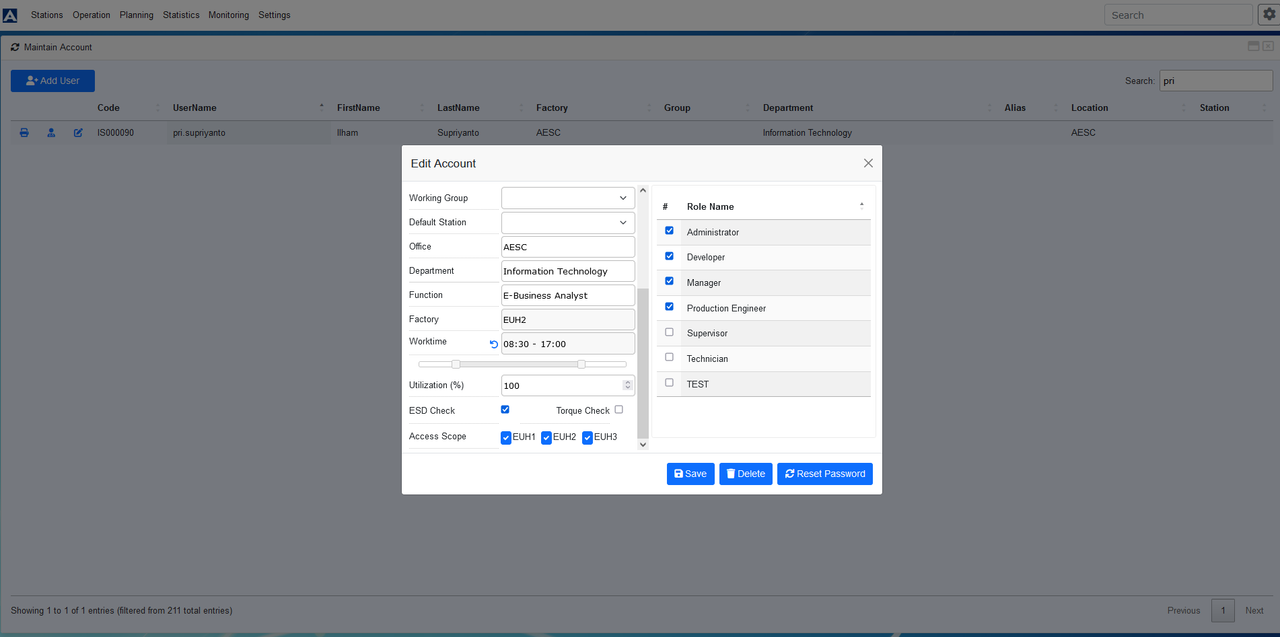
The user can be authorized for specific action and role in the system. For example, it can be Administrator or Manager and the user can have different actions related to this access scope. Also, only authorized people can have access to the sensitive data and for the different application, the person can have different role.
Infrastructure security
The IT team manages all corporate networks; performing maintenance and monitoring to safeguard the company’s information assets. Adequate monitoring is in place to ensure no unauthorized access to the corporate network takes place. Access to Advantech’s networks must only be granted via formal IT Request procedure defined in the IT Service Process. All access is removed for employees that have been terminated following the process specified in the IT Service Process.
The database is hosted on different server. And the security controls make sure that this server is accessible based on user and IP address.
Last updated